B.Sc. Computer Science (Cybersecurity)
Arab Academy for Science, Technology & Maritime Transport
GPA: 3.61/4.0 (Excellent)
Top 1% TryHackMe (300+ rooms and 40+ badges)
Professional Summary
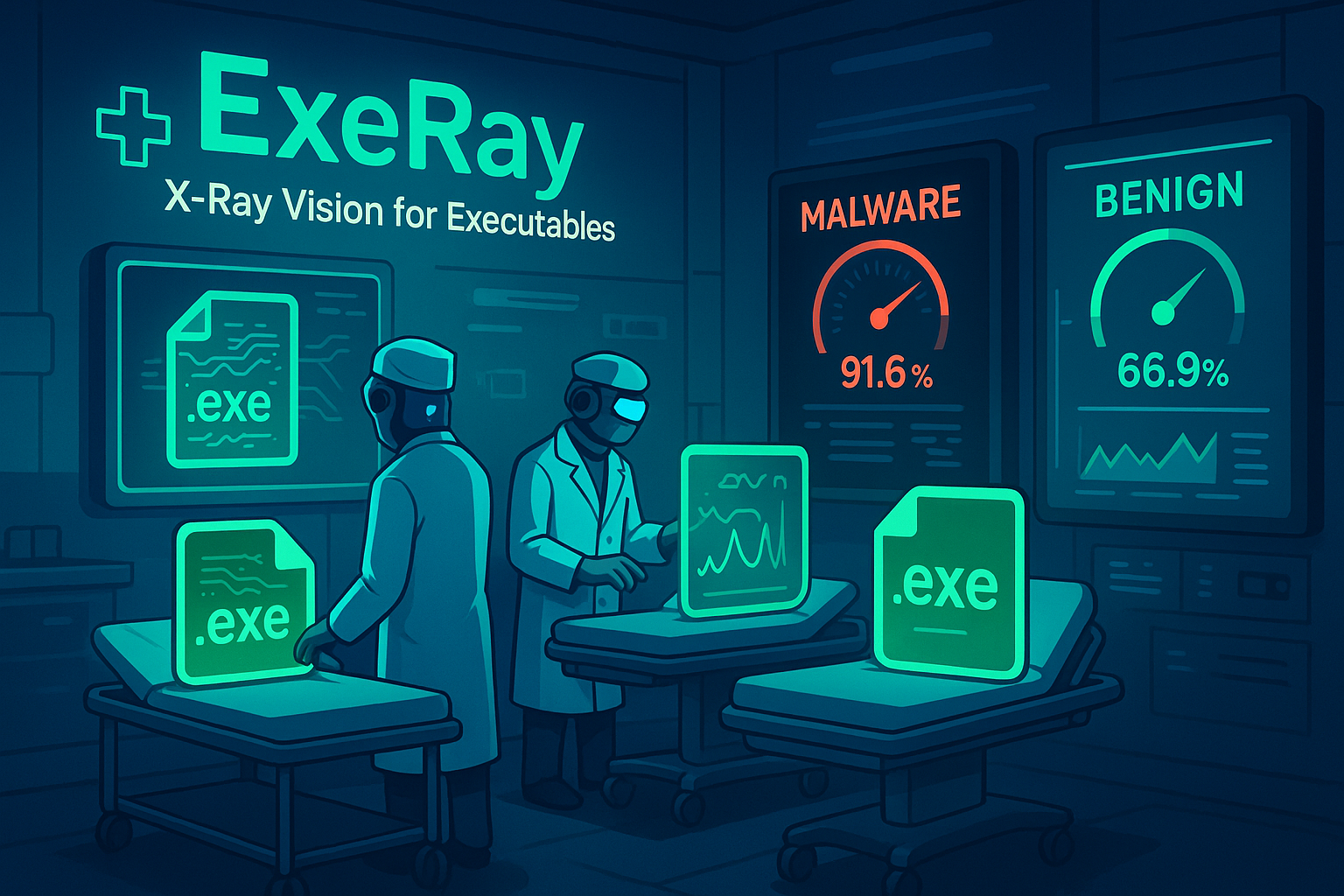
Cybersecurity student with hands-on experience in threat detection, malware analysis, and AI-driven security solutions. Currently developing DroneSentinel – an AI-powered security gap monitoring system as my graduation project.
Security Domains
SOC Operations, Threat Intelligence, Penetration Testing, Digital Forensics
Technical Skills
Python, Bash, Docker, ELK Stack, ML/AI, Terraform, Splunk
Experience
WE Innovate Bootcamp (SOC Analyst), NBE (IT Trainee), CIB (Intern)
Seeking opportunities to apply my skills in threat detection engineering and contribute to innovative cybersecurity solutions.